
Pixalate monitors and prevents 38 major types of invalid traffic (“IVT”), and there are times when we detect specific examples of sophisticated IVT that appear concrete and offer the opportunity to bring to light how fraud can work within the programmatic ecosystem.
In this case, Pixalate identified what we believe is a significant example of mobile app laundering that relies heavily upon Bundle ID spoofing. Laundering has been a growing problem in the mobile app space over the past 12 months, and it has become one of the most prevalent types of ad fraud.
Based on Pixalate’s data and research, this particular finding — which is linked to a single app — could be costing advertisers over $75 million per year, and several major brands may have been exposed.
Our research discovered that the MegaCast - Chromecast Player application appears to receive encrypted information from a third-party vendor called MobiAsset, which we believe serves as a catalyst for the mobile app laundering. MegaCast then links to a third-party vendor, called Mobilytics, as part of the ad call.
From the information communicated through Mobilytics, the inventory identification appears to have changed and is no longer MegaCast but, instead, references one of more than 50 identified applications, such as Lucky Jelly Puzzle or Survival Island: Primal Land. This laundering, which looks to us like an example of IVT where the advertiser believes they are buying inventory on one of the 50+ identified applications, but, instead, the ads may “render” in a dark screen or a background process which is not visible.
Mobilytics.org (not to be confused with Mobalytics or Mobalytics.gg) positions itself as a mobile app analytics platform. Mobilytics and MegaCast list the same address in Malta as their location.
MegaCast - Chromecast Player (Bundle ID: com.mega.cast) is the app in question.
Here is a video captured by the Pixalate analyst team detailing the apparent mobile app laundering in action:
The MegaCast - Chromecast Player app (referred to as “MegaCast” for the rest of this article) is an Android application available via the Google Play Store.
application available via the Google Play Store.
Here is a high-level explanation of what the app purports to do, extracted from their Google Play Store profile page:
"It is the first Chromecast player with real time transcoding support. It goes ever further than the possible [sic], and it CAN even PLAY files that Chromecast doesn’t support."
The app has over 1,000,000 (1 million) downloads, according to the Google Play Store. Its average user rating is 4 stars.
To get a sense of the potential revenue impact, we tracked activity across devices that had MegaCast installed. Here’s what we found:
Based on conservative estimates, we believe this discovery could be costing advertisers at least $75 million per year.
To see exactly how we arrived at this estimate, please refer to this shared Google Sheets document.
There appear to be a handful of different scenarios at play here. These are the three primary activities that we believe are occurring:
This blog post focuses on the first scenario: Mobile app laundering.
We’ve extracted screenshots from the Charles Log to depict how the mobile app laundering takes place — and what that looks like. Note: The below steps appear to take place whenever a phone that has the MegaCast app installed is powered on; we believe the phone does not need to be “awake” and the MegaCast app does not need to be open in order for these processes to occur.
Shortly after the user’s phone is turned on, the app sends a request to MobiAsset; and MobiAsset responds with an encrypted message to the device which we believe serves as the “activation” of the Bundle ID spoofing activity.
The below screenshot shows the encrypted message (you can also see this at the 1:04 mark in the video).
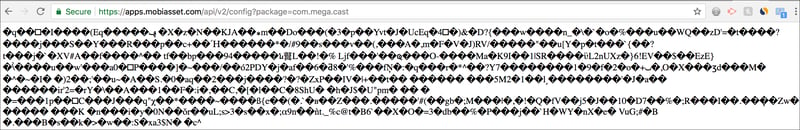
The information is encrypted, but it is possible that this is transmitting up-to-date ad ops-related information to MegaCast, such as the construction of ad calls, what containers should be used, etc. It’s also possible that this encrypted message contains information on which Mobilytics Config IDs are available.
Once it has all of the ad ops-related business squared away, the MegaCast app then begins communicating with Mobilytics, which brings us to Step 2:
We believe MegaCast then requests Mobilytics for information on what Bundle IDs to represent, after compiling a list of advertisers and platforms that are interested in the available inventory. This step takes place prior to sending the information to the monetization platform.
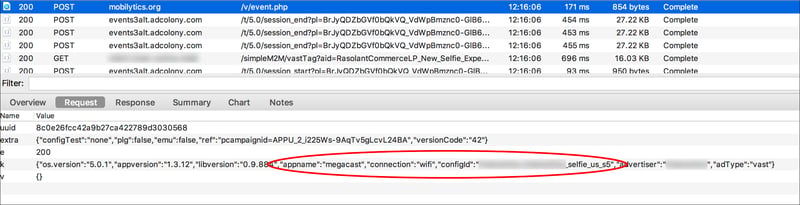
As seen above, the App Name is MegaCast, which shows where this call is originating from. However, the Config ID has been changed to selfie_us_s5.
MegaCast appears to notify the specified platform that inventory is available, and that platform starts fielding bids for the apparently-laundered inventory. The spoofed apps linked to the Mobilytics Config ID can always be linked to the “App Name” or Bundle ID in the corresponding ad server request.
In other words, the monetization platform (e.g., an SSP) thinks the inventory is coming from whatever app is being spoofed, even though it is still coming from MegaCast. All ties to MegaCast are scrubbed prior to the ad call reaching the monetization platform.
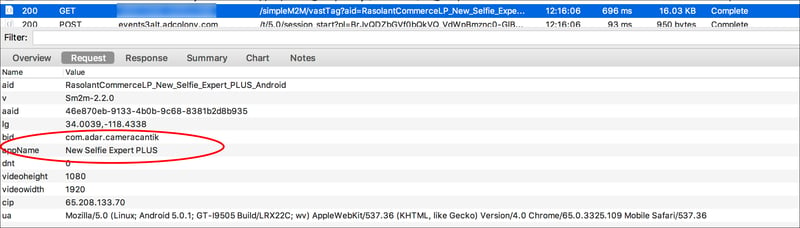
As you can see above, the monetization platform now thinks they are monetizing an impression from New Selfie Expert PLUS (Bundle ID: com.adar.cameracantik). This is the associated app from the Config ID that was inserted as shown in Step 1.
After the ad call has been assembled (Step 1) and the request for creative has been completed (Step 2), then an advertiser buys the impression and the ad is served, potentially just to a black screen. The below is the associated Charles Log screenshot for this particular impression:
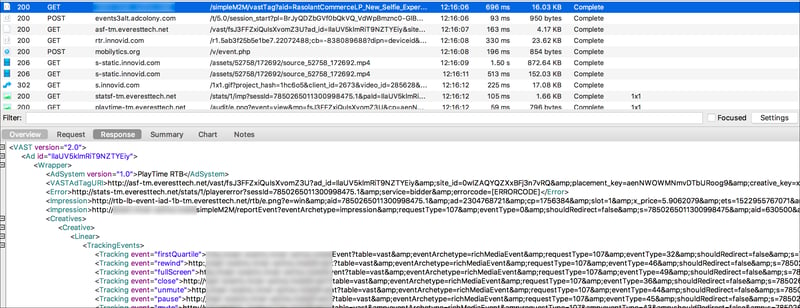
In this case, it was a video ad wrapped in a VAST tag. (This particular ad appears to have been for L’Oreal.)
The above screenshots show New Selfie Expert PLUS as the app that appears to be spoofed. Based on Pixalate’s observations, there are 50+ apps that appear to be utilized in the laundering, and the apps do not appear to be completely random. As seen in the Config ID that is changing upon ad calls (shown in Step 1 above), the app seems to be chosen specifically because it already has a relationship with the platform that goes on to monetize the ad. This could be done to reduce suspicion.
For example, in the above screenshots, it is possible that “New Selfie Expert PLUS” was selected because MegaCast was looking for inventory that is popular with their buying platforms, brand-safe, and a commonly seen pathway. In selecting such apps, it may be less likely that any red flags would be raised.
Facebook, Disney, and more were among the brands impacted by this discovery. This is a partial list, representing a snapshot of companies that we believe were victimized by the apparent invalid activity. You can download our whitepaper which shares network capture images as well as images of the creatives.
Pixalate is a cross-channel fraud intelligence company that works with brands and platforms to prevent invalid traffic and improve ad inventory quality. We monitor 38 major types of invalid traffic, viewability, brand safety, and other media metrics in order to deliver a complete measurement platform that facilitates any buying or selling goal. Pixalate specializes in detailed in-app, OTT and display analysis by offering fraud analytics for precise detection, pre-bid blocklists for custom prevention, and media ratings for media planning and review.
Want more data-driven insights? Sign up for our blog!
*By entering your email address and clicking Subscribe, you are agreeing to our Terms of Use and Privacy Policy.
These Stories on Mobile
*By entering your email address and clicking Subscribe, you are agreeing to our Terms of Use and Privacy Policy.
Disclaimer: The content of this page reflects Pixalate’s opinions with respect to the factors that Pixalate believes can be useful to the digital media industry. Any proprietary data shared is grounded in Pixalate’s proprietary technology and analytics, which Pixalate is continuously evaluating and updating. Any references to outside sources should not be construed as endorsements. Pixalate’s opinions are just that - opinion, not facts or guarantees.
Per the MRC, “'Fraud' is not intended to represent fraud as defined in various laws, statutes and ordinances or as conventionally used in U.S. Court or other legal proceedings, but rather a custom definition strictly for advertising measurement purposes. Also per the MRC, “‘Invalid Traffic’ is defined generally as traffic that does not meet certain ad serving quality or completeness criteria, or otherwise does not represent legitimate ad traffic that should be included in measurement counts. Among the reasons why ad traffic may be deemed invalid is it is a result of non-human traffic (spiders, bots, etc.), or activity designed to produce fraudulent traffic.”

